Strengthening AWS Security to Prevent Breaches
Services provided on this Project
Problem Statement
The company suffered a major data breach in its AWS cloud, exposing sensitive data. The breach highlighted gaps in access management, data encryption, vulnerability scanning, and compliance. To prevent future incidents, the company needed to implement DevSecOps practices, strengthen IAM policies, improve data encryption, and enhance threat detection and monitoring.
CLIENT
AlphaBravo Development
PROJECT SCHEDULE
Nov 2024 — Jan 2025
PROJECT SIZE
$50,000 to $199,999
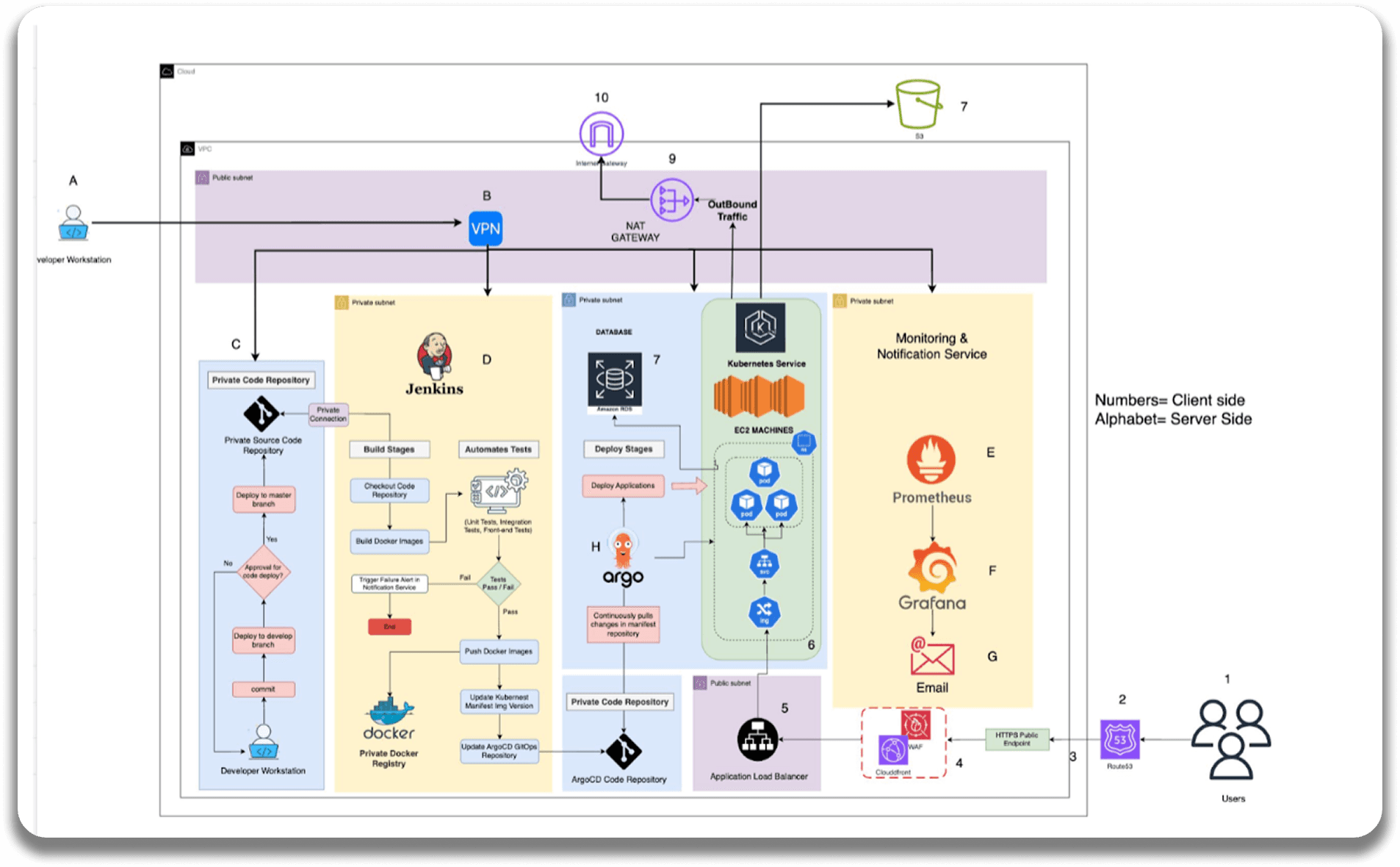
Proposed Solution
Private VPC
for resource isolation.
AWS VPN
Secured developer access.
IAM policies
Enforced least privilege with automated key rotation.
Secured CI/CD pipeline
with SonarQube and Trivy for vulnerability scanning.
AWS GuardDuty
Continuous threat detection and DDoS protection.
Applied data encryption
for both in-transit and at-rest data.
Managed secrets
with AWS Secrets Manager.

To improve AWS security, the solution focused on network security, access management, pipeline security, monitoring, and data encryption.
Core tech stack we work with
Leveraging the Leading Programming Languages and Frameworks to Deliver Reliable, Scalable Solutions.




Outcomes & Success Metrics
Significant reduction in scam calls, improved uptime, enhanced scalability, and efficient AI integration.